[ad_1]
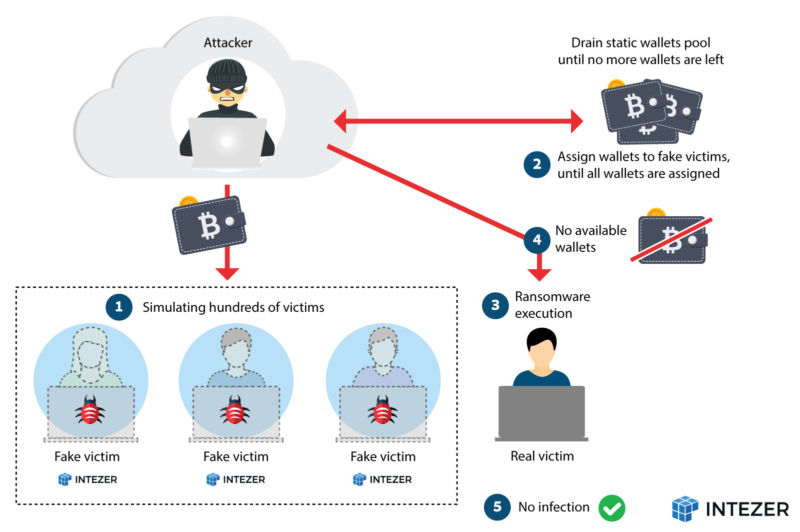
Enlarge / A diagram showing how a DoS shut down an ongoing ransomware campaign. (credit: Intezer)
Whitehats used a novel denial-of-service hack to score a key victory against ransomware criminals. Unfortunately, the blackhats have struck back by updating their infrastructure, leaving the fight with no clear winner.
Researchers at security firm Intezer performed the DoS technique against ransomware dubbed QNAPCrypt, a largely undetected strain that, as its name suggests, infects network storage devices made by Taiwan-based QNAP Systems and possibly other manufacturers. The hack spread by exploiting secure shell, (or SSH) connections that used weak passwords. The researchers’ analysis found that each victim received a unique bitcoin wallet for sending ransoms, a measure that was most likely intended to prevent the attackers from being traced. The analysis also showed that QNAPCrypt only encrypted devices after they received the wallet address and a public RSA key from the command-and-control server.
Intezer researchers soon noticed two key weaknesses in that process:
Read 4 remaining paragraphs | Comments
[ad_2]
Source link
Related Posts
- Cox Internet now charges $15 extra for faster access to online game servers
- Comcast usage soars 34% to 200GB a month, pushing users closer to data cap
- After White House stop, Twitter CEO calls congresswoman about death threats
- The sim swap the US isn’t using
- Probable Russian Navy covert camera whale discovered by Norwegians
